There are two problems common security conferences, and general public, you can protect yourself against certain basic security measures. Security of the conference is increasingly important as more people not only attend these conferences, but also work remotely in general.
I will examine two conference security issues you may encounter the next time you're looking to connect to public wifi that was provided, or use a public computer room that is set up for your use
cybersecurity Conference :. Keyloggers
keyloggers are installed on computers for public use in cafés, conferences and other public places computer. These malicious pieces of strokes hardware and key software logs that are then used to recover the password, credit card numbers and bank account details.
They are not hard to find or expensive either. They even advertised on Twitter as they have legitimate uses:
Here are 5 Free #Keyloggers To save all your #Keystrokes! http://t.co/cgB6Jc0dPJ
- Open Source For You (@OpenSourceForU) 4. August, 2014
to protect against keylogging, there are two things you can do. The first is that which will now be obvious, check the hardware keylogger on the back of the computer. If you expect to find something that looks manifestly ill, or as a piece of pirated material together, you'd be wrong. Here is a picture of a harmful keylogger from a trusted source ...

... Amazon. These things are not hard to find!
They will be attached to the back of the computer between the keyboard and the usual place where the keyboard plugs. If you see it, you can risk to unplug and hoping that the software is still able to capture data.
This is the easy way, but we do not always get the easy option. Many keylogging activities are performed in the computer software so there is no way to see the device. How you can work around this problem is to bring along a USB key that has both an anti-keylogging software installed, and the applications you want to use. Buy a big stick, you can get 32GB fairly easily, if you have multiple applications you want to run.
Almost felt bad to miss a conference on local security because it is a weekend, then heard the cell service was hacked. Better off at home
- Rob Nelson (@ rnelson0) June 11, 2016
Cybersecurity Conference :. Man in the middle attacks
a man in the middle attack is when a hacker sets up a nice free internet. At a conference this can be a major problem as you can be surrounded by many free wifi connections. The conference could have the hotel in the conference center could have the local coffee could have one, and a number of exhibitors could have.
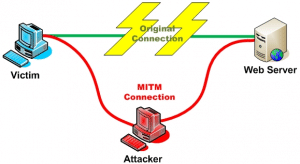
Encountering which is "free" is not uncommon. Many people want you to win your favor at conferences, and some free wifi is a good way to go. Hackers are aware of this and they offer their own free wifi - but it is not free at all
When you connect to free wifi hackers, violating the worst cybersecurity conference action, they can then intercept any and all information that you send or receive on the connection. Every business data bit could be someone else's virtual hands.
You can your own cybersecurity conference against man in the middle attacks at a conference, or anywhere public, using -ranked VPN Service . A VPN service will be able to encrypt your data before it gets to the "man in the middle", and it is impossible for even the most sleuthy hackers to steal your information.
At # pbevent blogging conference and my hacked account. Grrrrr !!
-. Tine (of @fortheloveofme) August 13, 2015
picture Conference Wesley Fryer
Keylogger picture Wikimedia Commons equipment.
man in the picture hack Wikimedia Commons environment.

0 Komentar