Encryption How Internet Works - The Basics
Everyone, no matter who they are, needs online encryption. It is not for the "bad guys", it is good for people looking to protect their information and keep it private. This may include your banking information, job information, and your personal email. You have the right to privacy, and encryption is how you get online.
If you want to learn how the Internet works encryption, in the simplest form, read on to see how it started, where it is today, and learn a basic understanding of how it works today.
How does the Internet encryption
The most fundamental thing about the Internet encryption that people are familiar with is that little green padlock in the left side of your browser:

means the little green padlock that the site HTTPS encryption , the most secure encryption of basic types online. Before going into the details of how the Internet encryption works, I want you to look for the lock before doing anything that you would rather private. The URL will also start with HTTPS.
based encryption modern Internetuses "public key encryption." It was developed in 1973 by GCHQ. Now GCHQ are the "good guys", they are like the English CIA, but it's still a bit risky as to what they can and can not decipher.
key functions of public Internet encryption on the fact that it is much harder to understand the factors of a given number - the numbers that were multiplied together to produce -. it really is to multiply the number
This means that it is easier to do the multiplication as understand what was multiplied. As if I were to ask you now what are the first two numbers multiply to give you 517? Can you guess?
...........................
is 47 x 11. A computer can multiply these numbers easily, but he can not understand numbers to multiply when given the number easily.
which then makes the Internet work encryption and public key encryption, in particular, generates large numbers and complex that only your computer and the computer or server that you connect knows the answer to. These large and complex figures that actually uses your browser when you see padlock - the number is the padlock. The greater the number, the higher the padlock is in theory.
When you access a Web site that has this green lock you two exchange this complex number and its solution. and the other site you Only you know what is happening on the connection now because only the two of you have the key -. the answer to the equation
 Internet encryption benchmarks
Internet encryption benchmarks
encryption key how the Internet works in terms of strength comes down to the number of digital bits that it uses to generate the number and the type of encryption used. In the early days of the Internet encryption standard was the key to 40 bits coded using the RC4 encryption. Anyone with knowledge and time could crack that encryption in moments now. The standard today is 256 bits or more, which should take centuries or even thousands of years to crack using conventional methods.
Some of the best VPN providers we review use encryption even higher than that, offering you even more protection you browse the Internet, do banking online, and posts nasty things to your significant other. You can learn more about VPN encryption protocols in the link.
Cracking modern encryption Internet
As you have probably heard, the NSA and GCHQ work hard to snoop into your private information. They spend millions of your tax dollars to build chips that can crack some encryption levels when given time.
Modern pirates are now trying to use graphics processing units that make your computer work to crack passwords. Most hacks occur hacks via brute force password cracking the actual encryption of the Internet.
This means that instead of trying to break the lock, they try to convince the Internet that you are stealing passwords through guessing with the software. The best software can make assumptions about 8 billion per second, cracking passwords up to 55 characters. After reading this you will know how the Internet encryption works, and I know that passwords are now the weak point, you need to work on!
image feature andrey_I / Shutterstock
Lock by LHF Graphics / Shutterstock
 bandwidth usage as video streaming tools. The problem is compounded when ISPs choose to take it on the specific Internet traffic, as with Comcast and others bottomed return rates in 2014.
bandwidth usage as video streaming tools. The problem is compounded when ISPs choose to take it on the specific Internet traffic, as with Comcast and others bottomed return rates in 2014.  Each browser has a private browsing option. This includes the main actors:
Each browser has a private browsing option. This includes the main actors:  If you leave a tab open for Facebook, they follow you. This is also true of Google, Amazon, Twitter, and almost all other online services "free." They make you tracking and sales data to advertisers money.
If you leave a tab open for Facebook, they follow you. This is also true of Google, Amazon, Twitter, and almost all other online services "free." They make you tracking and sales data to advertisers money. 
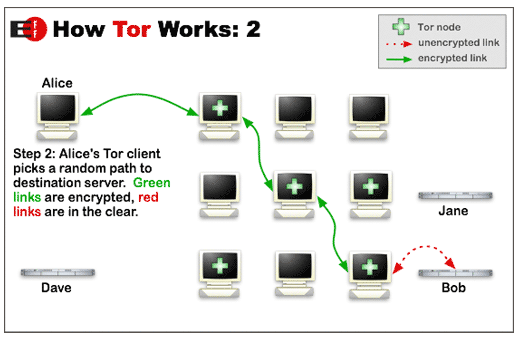
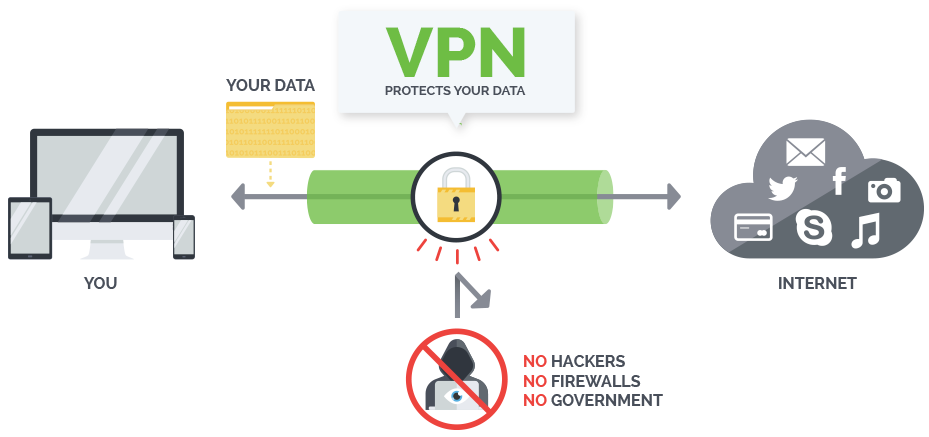
 When comparing vs Tor VPN, here are the main strengths now all your online activities, everything you do on the connected machine will be encrypted and anonymous. VPN:
When comparing vs Tor VPN, here are the main strengths now all your online activities, everything you do on the connected machine will be encrypted and anonymous. VPN:  Here are --other websites which currently use two-step authentication
Here are --other websites which currently use two-step authentication  4. Protect your online data with a VPN
4. Protect your online data with a VPN  A kill switch VPN make sure your real IP address, the IP address you are trying to hide, never exposed if the connection between you and the VPN server fails. How it does this is by cutting your internet connection when a connection loss occurs between the VPN server and your computer.
A kill switch VPN make sure your real IP address, the IP address you are trying to hide, never exposed if the connection between you and the VPN server fails. How it does this is by cutting your internet connection when a connection loss occurs between the VPN server and your computer. 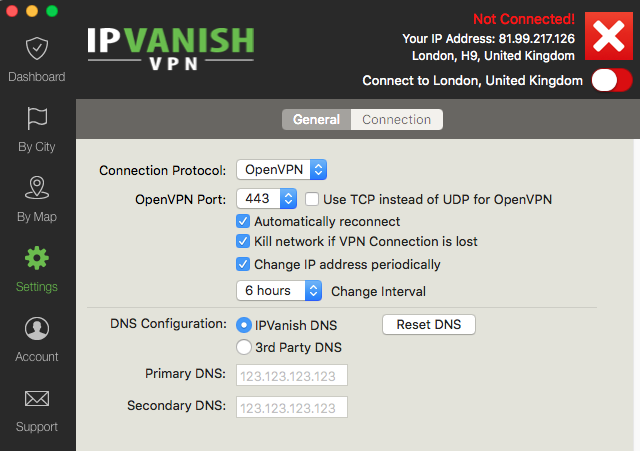
 the kill switch to PureVPN
the kill switch to PureVPN  service that requires knowing your identity.
service that requires knowing your identity.  There has been much speculation about the stability of currencies and online cryptocurrencies. As with all new things, there were growing pains along the way and an accident or two. The general trend with Bitcoin is now in place and the lower value of the currency plunged as low as in the past.
There has been much speculation about the stability of currencies and online cryptocurrencies. As with all new things, there were growing pains along the way and an accident or two. The general trend with Bitcoin is now in place and the lower value of the currency plunged as low as in the past.  Bitcoin Wikimedia Commons. Jay and Bey Wikimedia Commons.
Bitcoin Wikimedia Commons. Jay and Bey Wikimedia Commons.  the first reason why you would hide your IP is to prevent people from following you online. Have you ever wondered why you can visit a website, then go to one of your social media accounts and see ads for that site? You be followed, and most likely via your IP address.
the first reason why you would hide your IP is to prevent people from following you online. Have you ever wondered why you can visit a website, then go to one of your social media accounts and see ads for that site? You be followed, and most likely via your IP address.  See our own IP address tool. Do you see how our tool knows exactly where you are if you are not using a tool to change your IP address? Creepy, is not it?
See our own IP address tool. Do you see how our tool knows exactly where you are if you are not using a tool to change your IP address? Creepy, is not it?  protect
protect  The second aspect of the safety of the workforce is securing data flows. This is twofold:
The second aspect of the safety of the workforce is securing data flows. This is twofold:  Know when to update the software
Know when to update the software 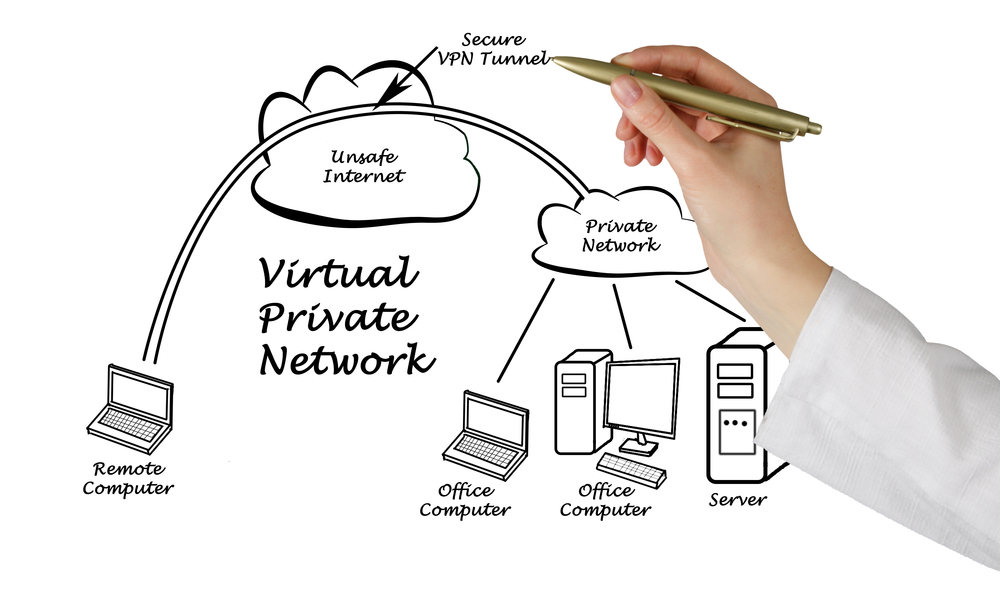 The most uses common to include a VPN.?
The most uses common to include a VPN.?  I wrote earlier about slow connection problems with Netflix. In this article, it was found that ISPs slowing connections to Netflix -. Most of the time just to mess with Netflix that these ISPs were owned by cable companies saw them as competition
I wrote earlier about slow connection problems with Netflix. In this article, it was found that ISPs slowing connections to Netflix -. Most of the time just to mess with Netflix that these ISPs were owned by cable companies saw them as competition  ISPs are so helpful - they allow you to either rent a modem from them, or outright buy one of them. Is not that nice? For only $ 10 / month, you too can have your own speed, modem status of art. Or you can buy them! WOW!
ISPs are so helpful - they allow you to either rent a modem from them, or outright buy one of them. Is not that nice? For only $ 10 / month, you too can have your own speed, modem status of art. Or you can buy them! WOW!